Credentials File Encryption
NetObserv Trap supports easy and secure trap listener credentials file encryption using SOPs and industry-standard AGE.
Getting Started
Environmental Dependencies
-
Ensure sops is installed in your local environment:
# Change sops-v3.8.1.linux.amd64 if needed based on your environment
curl -LO https://github.com/getsops/sops/releases/download/v3.8.1/sops-v3.8.1.linux.amd64
sudo mv sops-v3.8.1.linux.amd64 /usr/local/bin/sops
sops --version # to verify install -
Also ensure age is installed in your local environment to edit via CLI:
sudo apt install age # Debian based linux
brew install age # macos
age --version # to verify install
Trap Listener Credentials Encryption Configuration
Please visit Trap Listener Credentials Encryption to learn more.
Recommended Usage
Always keep a secured backup of a non-encrypted version of the credentials file in case of any issues.
Setup
The easiest and most recommended way to get started is to simply set the following as below:
EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_ENABLE=true
EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_CREATE=true
EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_PASSWORD="YourPassword"
EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_PRIVATE_KEY_FILE_PATH="/etc/elastiflow/trap/.age/key.age"
EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_PUBLIC_KEY_FILE_PATH="/etc/elastiflow/trap/.age/public-age-keys.txt"
The following behavior will occur when the Trap collector is next restarted:
-
Generate password protected age keys at the configured credentials file paths.
-
Encrypt trap listener credential yaml files using those keys.
Once successfully encrypted with sops, the following listener credential file:
credentials:
users:
- username: myuser2
authentication_protocol: md5
authentication_passphrase: mypassword2
privacy_protocol: aes
privacy_passphrase: myprivacy2
authoritative_engine_id: authoritative_engine_id
- Will resemble the yaml below if using the default
sopssetting forEF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_TYPE:
credentials:
users:
- username: ENC[AES256_GCM,data:B052jkhy4g==,iv:pcfami0QKG4TNRDre56mPUMyohUbnhUpZftAbZlRAFk=,tag:5EimGwktVw/GQ7kYj0k4rA==,type:str]
authentication_protocol: ENC[AES256_GCM,data:LSfR,iv:Afp733FCUgvsgXJ7TBMa++W/fTNk8H68lGp/VYzaf70=,tag:JiORrsCG4I//uaygFWiIIQ==,type:str]
authentication_passphrase: ENC[AES256_GCM,data:EuKcz8vsM5z5wAE=,iv:0GSAxu5/hn8OVoCIGrUGInvxGoY/frlJIXqTjDN9i3s=,tag:chIwUWMppBh9Olg26GwkOw==,type:str]
privacy_protocol: ENC[AES256_GCM,data:9xyn,iv:vZw9m8W23yMyeOa9eXJIeGSy+IbddjbBoFXL4XVA3MI=,tag:IGMgiRLETWdfPO1VY6sGxA==,type:str]
privacy_passphrase: ENC[AES256_GCM,data:7aQ5a0RAaBTEAQ==,iv:GzfYtnmMzvB4SrtZPAXHfjXuegFcuiMIW7pGJmXSIhc=,tag:J4BjEYX5RzW4ZkcBOooIqQ==,type:str]
authoritative_engine_id: ENC[AES256_GCM,data:ILoVUxpuDvQy/c67DkxswEHsxgsi5ck=,iv:e8Kctcdbo18T+wvA0oNqSCDfNRdtO1WKS1ATuGKVSuU=,tag:L8ggZusCIfFLFdPM8eSXIw==,type:str]
sops:
kms: []
gcp_kms: []
azure_kv: []
hc_vault: []
age:
- recipient: age1ln04w90q920hqw0zhgqftlh3ckprcgdvq0dpvv87hnpxn3plv3tqx6xfqt
enc: |
-----BEGIN AGE ENCRYPTED FILE-----
YWdlLWVuY3J5cHRpb24ub3JnL3YxCi0+IFgyNTUxOSBBRnNWM0toYzN3Z2FTWnRY
RmdHM0dRSThMdXFQYWNpNjU4QmUzdkZmeldVCnZIS2pueHY1c0tzUGgxa2IzTGwz
NGptai9nYy9sY1pRN2NPc0VvR0JLZmMKLS0tIHRqbVpVc3h4c01DT2trcjJpUTNa
SkZmcFozSks0bEdsVS9uakc5YWtTZkUKak/51Zc6OoBPfqKNxqctmQAtfgi2/tDe
OA0fPdh1cWrjbeNGkLsF9w4rV48LDmPEEyfoclhO0WRjsJLu8/vi1w==
-----END AGE ENCRYPTED FILE-----
lastmodified: "2024-09-29T05:19:18Z"
mac: ENC[AES256_GCM,data:mirziSe8s+WUBs0k/A8GvJeo01HRBgWzVukqLyzUPkmRQMeMJDlYoSM9e9pHGZXchhq5Ech0eGbXo4cR9EP8lockdnHOsjHsAkRfzBUDJXVB9u5b6CvHfHBmRHUttOkA058+b8hla3T1nh/cVPBwI5woDoIuTBE3fp0idM6tHHw=,iv:dI3p5N8OmpZOD2kevZXCDO4fBaxy2g7ZmSBM6QTO6PQ=,tag:gMe+zE7i1dtl20WKM1MNbw==,type:str]
pgp: []
unencrypted_suffix: _unencrypted
version: 3.8.1
-Otherwise, if EF_INPUT_TRAP_LISTENER_CREDENTIALS_SECURE_STORE_TYPE is set as standard, the entire file will be encrypted:
age-encryption.org/v1
-> X25519 K+YTITCvJ9Am1U/jEdCCpCqxBbXTvb4gMcuDhUAbcHc
pdbTI+71EOdHZfhjk+hjuBSxYrcmcS88Quxu7+jsfns
--- T9MMrZ9tjvN2Lf4pWevQDkGZrAw44JRHqFNWPqTi9D8
�%5RIa-���mpa �0�|e���<7
+��.C0
�
�\.K�Q�k?1d��d���^���%�
����-�y@�k.�{ĺ�L�S
3?\k��2ż
���Ie�� O�Q�ZR� P���2�Wb1�ͧ�i��%�
z
r
{�sk
�BT���
��0��e�Z�J$V��7$�7AʽZ���Q�^R��Cʹ��}\-�յ״Q�aګT�̫[���1q�ގ)n�Z|T4v��n� j��@V}[��%7f
DwQ�9Л��*��ۗ�����|d��!~�
Editing Encrypted Files
SOPs
Encrypted files should not be manually edited without using the SOPs CLI editor.
To securely edit trap listener credential files, please use the SOPs CLI:
-
Non-password protected private key:
SOPS_AGE_RECIPIENTS=$(</etc/elastiflow/trap/.age/public-age-keys.txt) \
SOPS_AGE_KEY_FILE=/etc/elastiflow/trap/.age/key.age \
sops credentials/credential.yaml -
Password protected private key:
SOPS_AGE_RECIPIENTS=$(</etc/elastiflow/trap/.age/public-age-keys.txt) \
SOPS_AGE_KEY=$(age -d /etc/elastiflow/trap/.age/key.age) sops credentials/credential.yaml
These commands will decrypt the file in memory and open with a text editor of your choice. By default, the editor used will be vim:
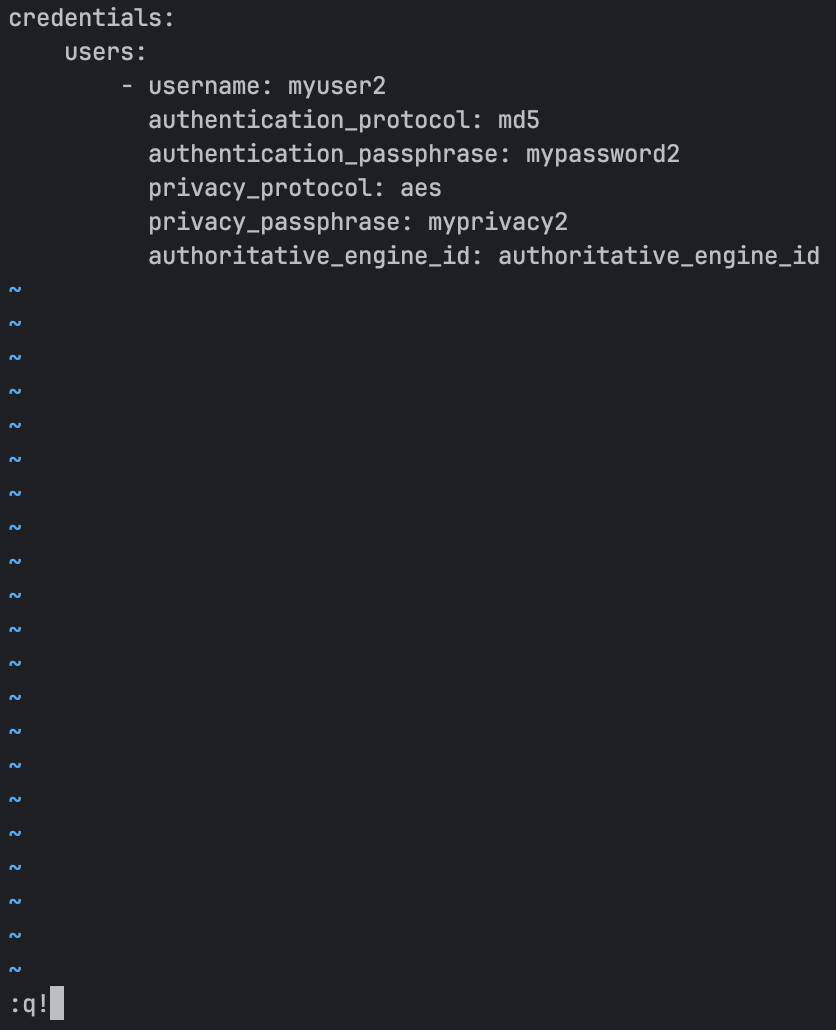
-
Using nano instead of vim:
EDITOR=nano \
SOPS_AGE_RECIPIENTS=$(</etc/elastiflow/trap/.age/public-age-keys.txt) \
SOPS_AGE_KEY=$(age -d /etc/elastiflow/trap/.age/key.age) sops credentials/credential.yaml
Once changes are made, save and exit to update the encrypted file stored on the disk drive.
Standard AGE
To securely edit trap listener credential files, please follow the below steps:
-
Decrypt the file:
age -d -i /etc/elastiflow/trap/.age/key.age -o ./credentials/credential.yaml ./credentials/credential-dec.yaml -
Edit the decrypted file using your preferred text editor.
-
Encrypt the file:
age -r "$(cat /etc/elastiflow/trap/.age/public-age-keys.txt)" -o ./credentials/credential-dec.yaml ./credentials/credential.yaml -
Remove the decrypted file:
rm ./credentials/credential-dec.yaml -
Restart the Trap collector to apply the changes.